Cloud Provider Fends Off Record-Breaking DDoS Attack

A group of high-capacity routers may have been hijacked to launch a record-breaking DDoS attack on a cloud provider back in April.
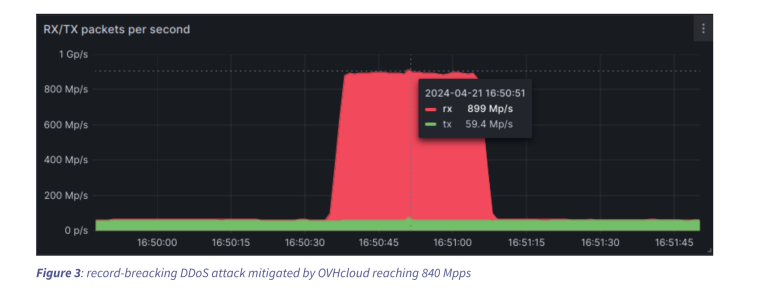
The attack targeted France-based OVHCloud, reaching 840 million packets per second. The number surpasses the 809 million packets per second (Mpps) attack that DDoS protection provider Akamai experienced in 2020 when a hacker tried to take down a European bank.
DDoS attacks overwhelm an internet service with traffic, knocking it offline. Over the years, cybercriminals have come up with various ways to launch DDoS assaults, which can include summoning terabits of data per second or millions of requests per second.
In OVHCloud’s case, the attacker leveraged a “packet rate attack,” which can overload the packet processing engines to a web property’s networking devices rather than merely deplete the available bandwidth.
“The general idea is to cripple the infrastructures in front of the targeted service (e.g., load-balancers, anti-DDoS systems, …), thus possibly impacting a large infrastructure as collateral damage. Simply put: instead of trying to find holes in anti-DDoS systems, just take them down,” OVHCloud says.
Most packet rate attacks usually rate well below 100Mpps, since a large amount of computing power is needed to generate so many packets. But in the past 18 months, OVHCloud has detected an increase in packet rate attacks reaching over 100Mpps. “We went from mitigating few of them each week, to tens or even hundreds per week,” the company said.
The April attack that reached 840Mpps originated from 5,000 IP addresses. OVHCloud didn’t reveal what the attack attempted to take down. However, the company said it had enough internet capacity to fend off the assault.
To investigate the source, OVHCloud looked at DDoS attacks it encountered ranging from 100 to 500Mpps. The company then traced some of the activity to a group of high-capacity MikroTik routers, which may have been hijacked to launch the DDoS assaults.
OVHCloud points to how MikroTik routers have suffered from vulnerabilities in the past. Many of the affected devices also operate with an interface openly accessible over HTTP. In addition, OVHCloud has uncovered evidence that 99,382 MikroTik routers are currently online, with the capacity to launch high packet rate attacks.